Cars are now software-defined, connected, and constantly updated, expanding attack surfaces across the In-Vehicle Network (IVN), mobile apps, and cloud backends. Regulators add urgency: the UN’s Cybersecurity Management System (CSMS) requirement in UNECE Regulation No. 155 and secure Over-the-Air (OTA) updates in UNECE Regulation No. 156 set lifecycle obligations, while ISO/SAE 21434 defines the engineering “how.”
This article distills ten automotive cybersecurity best practices you can implement now: a living Threat Analysis and Risk Assessment (TARA), a rigorous Secure Software Development Lifecycle (SSDLC), hardening for boot chains and networks, fleet-scale secure OTA, and continuous monitoring via a Vehicle Security Operations Center (vSOC), all tied to Software Bill of Materials (SBOM)-driven vulnerability management and strong supplier assurance.
Our goal is pragmatic: cut risk where it counts, prove it with metrics, and keep pace with evolving threats. At Svitla Systems, we help automotive leaders turn these practices into repeatable routines, so security improves release by release, not once a year.
Development of Automotive Technology and the Current State
Cars run on software and constant connectivity. They interact with phones, infrastructure, and cloud services. This evolution increases risk across vehicles, backends, and mobile apps.
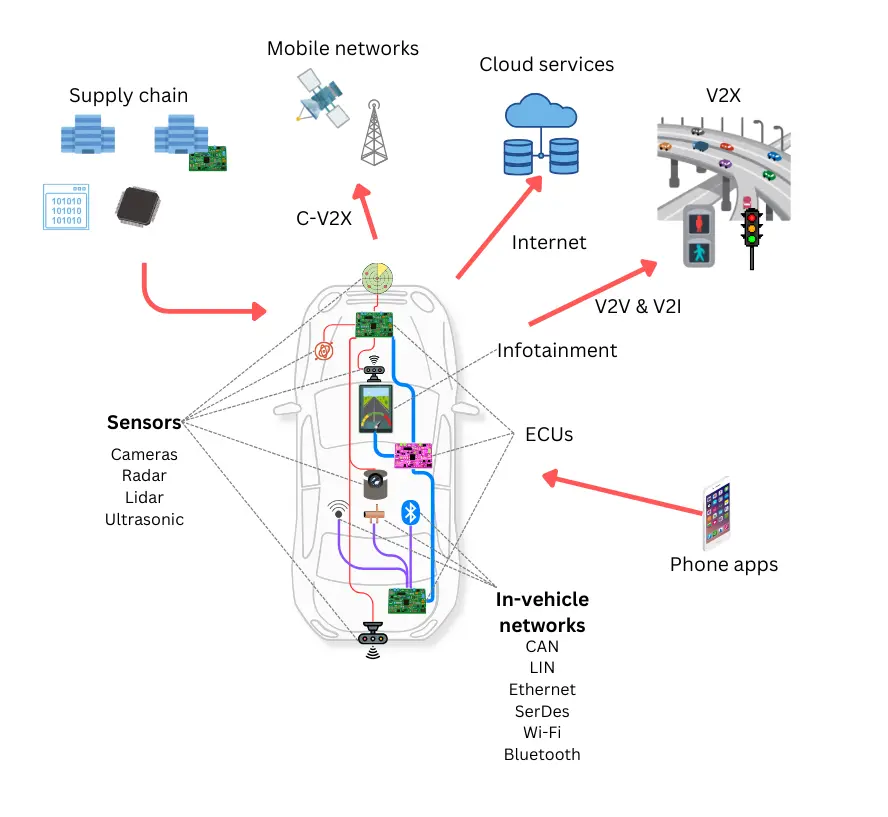
Source: Keysight
EU policy accelerates the shift to cleaner and safer mobility. From 2035, only zero-emission new cars and vans can be registered. By 2030, targets aim to cut CO₂ emissions by 55% for cars and 50% for vans. The updated General Safety Regulation has been in effect since July 6, 2022. It created a legal path to approve automated driving systems. UNECE R155 and R156 require a Cybersecurity Management System and secure Over-the-Air updates. The rules apply to new type approvals since July 6, 2022, and to all new vehicles since July 7, 2024.
Key automotive technology trends
Connected cars. These vehicles link to the internet and nearby devices. Drivers get real-time navigation and traffic awareness. Remote diagnostics reduce the need for workshop visits and expedite repairs. Emergency calling improves response times after incidents. Smartphone integration extends features into everyday use.
Autonomous vehicles. Automation combines sensors and intelligent software. Radar and lidar map the surroundings in poor visibility. GPS and odometry support precise positioning. Computer vision detects lanes, signs, and obstacles. Most vehicles deliver partial automation today. Whole Level 5 autonomy remains a long-term goal.
Driver assistance technologies. Advanced systems reduce crashes and fatigue. Automatic emergency braking reacts faster than humans. Lane keeping reduces drift during long trips. Adaptive cruise control manages speed and distance smoothly. Blind-spot monitoring helps with safe lane changes. Together, these features raise comfort and safety for everyday driving.
The Importance of Automotive Cybersecurity + Vehicle Cybersecurity Standards
A Cybersecurity Management System is the operating backbone. It aligns people, processes, and tools across engineering and operations. It turns policy into daily routines and measurable results.
UNECE WP.29 R155 sets what must be in place. It requires a working CSMS and proof that it reduces risk. It covers development, production, and post-production. It also expects incident handling and continuous improvement. The rule applies to new vehicle types from July 6, 2022, and to all new vehicles placed on the market from July 7, 2024, across UNECE contracting markets, such as the EU.
UNECE WP.29 R156 focuses on software updates. It demands secure Over-the-Air updates and controlled rollbacks. It also requires records that show each update was authorized and verified. Its timing matches R155 for new types in July 2022 and all new vehicles from July 2024.
ISO/SAE 21434 outlines the principles for engineering cybersecurity throughout the lifecycle. It covers threat analysis, design controls, verification, release, operation, maintenance, and decommissioning for electrical and electronic systems in road vehicles. First published in 2021, it is the primary engineering reference paired with the UNECE approvals.
Together, these create one map. R155 and R156 define obligations and evidence. ISO/SAE 21434 provides the workflows to meet them.
Audits and evidence keep teams honest. Maintain a live TARA, signed design decisions, test results, and incident logs. Track update provenance, key management, and IDS baselines. Prove effectiveness with metrics across the vehicle lifecycle.
10 Cybersecurity Best Practices in Automotive
Pillar 1. Risk-driven engineering
Conduct a Threat Analysis and Risk Assessment (TARA) at every phase of the lifecycle, starting from concept and continuing through design, validation, release, and in-field operation. Keep it current with incident reports and trusted threat intelligence so it functions as a living system rather than a one-time document.
Prioritize risks by safety impact and exposure across the entire architecture. Critical domains such as braking, steering, powertrain, and charging come first, followed by exposed interfaces that include telematics, Bluetooth, Wi-Fi, cellular, Diagnostics over Internet Protocol (DoIP), and Vehicle-to-Everything (V2X). Model realistic misuse cases and end-to-end attack paths, then bind each high-priority risk to a specific control and a verifiable test.
Define acceptance criteria that are clear, measurable, and tied to security gates in CI, as well as to safety goals and compliance needs. Record residual risk and obtain explicit sign-off from accountable owners, then update the design when new data appears and close the loop through verification, telemetry, and post-release review.
Track outcomes using a concise set of metrics that clearly show progress. Monitor the freshness of the risk register, the time to close high-severity items, and the share of high-risk findings that have now been implemented and verified controls.
Pillar 2. Secure software development lifecycle (SSDLC) for ECUs and backends
Bake security into every stage, from requirements and threat modeling to code reviews and release. Add automated checks to CI and CD so each build runs static and dynamic security tests, and block merges that increase risk or fail agreed gates.
Use proven coding standards where they fit. MISRA C and CERT C help prevent memory and concurrency bugs in ECU code, and the same discipline should cover infrastructure as code and build pipelines.
Treat cloud and telemetry services as part of the vehicle surface. Harden APIs and authentication, enforce least privilege, and log security events in a format your vehicle operations team can act on. Track outcomes with a small set of metrics such as first-pass gate success, time to fix high-severity findings, and regression re-open rate.
Pillar 3. Cryptography, identities, and trusted boot chain
Establish a strong foundation of trust so that every ECU starts in a well-defined state. Use secure boot that verifies signed firmware at each stage, utilizing hardware-backed keys stored in a Trusted Platform Module (TPM) or a Hardware Security Module (HSM). Give each ECU a unique identity and enforce mutual authentication for IVN, telematics, and service tools. Plan certificate rotation and revocation from day one so keys never live longer than they should.
Protect secrets across the whole lifecycle, not only on the vehicle. Secure key generation, storage, and injection throughout the manufacturing process. Lock down service tooling with strong authentication and role separation. Harden the Over-the-Air update pipeline with signing, provenance checks, and protected build systems. Log every sensitive action so audits can trace who did what and when.
Operate the system as you ship updates. Rotate certificates on a defined cadence, roll keys safely when compromise is suspected, and block outdated identities. Test recovery paths, including rollback after a failed verification. Track simple metrics such as the share of ECUs with hardware-backed keys, the rate of verified boots, median time to rotate keys, and the percentage of updates that pass signature checks on the first attempt.
Pillar 4. Network segmentation and interface hardening
Split the in-vehicle network into clear domains. Keep powertrain and advanced driver assistance systems (ADAS) isolated from infotainment and telematics. Route traffic through secure gateways that enforce allow-lists and protocol rules. Add message authentication, freshness, and rate limits to stop spoofing and floods.
Treat every interface as a potential entry point. Harden DoIP and unified diagnostic services (UDS) with access control, role-based permissions, and secure routines. Secure Wi-Fi, Bluetooth, cellular, and V2X connections with strong authentication and well-maintained stacks. Disable unused services and debug ports before production.
Test like an attacker before each release. Run conformance tests and negative testing. Fuzz protocols at realistic speeds and payload sizes. Validate that gateway filters block cross-domain traffic that should never pass.
Track simple metrics to prove progress. Monitor blocked unauthenticated frames per thousand kilometers. Measure interface conformance pass rates and the share of interfaces fuzzed this cycle. Record time to patch interface vulnerabilities and watch IDS false-positive rates.
Pillar 5. OTA with rollback and fleet-scale patching
Secure every step of the update path so only trusted code reaches the vehicle. Sign images in a protected build system, store keys in hardware, and verify provenance on the device before any write occurs. Use fail-safe layouts such as A and B partitions so the system can boot from a known good image when verification fails.
Design rollback as a first-class capability. Keep previous images available, validate them before switching, and record the reason for any rollback so that engineering can identify and address the root cause. Protect delta updates and metadata with the same rigor as full images, since attackers will target the weakest link.
Run updates as managed campaigns, not ad hoc pushes. Start with small canary groups, monitor telemetry for safety and performance signals, and then expand incrementally across models, regions, and hardware variants. Set clear service levels for critical fixes and publish a patch calendar so that product, support, and partners can plan accordingly.
Prove effectiveness with a few numbers. Track fleet patch coverage, mean time to patch for critical issues, rollback success rate, and the share of vehicles that verify signatures on the first attempt.
Pillar 6. SBOM-led vulnerability management and supply-chain assurance
Create a Software Bill of Materials for every ECU and backend service and keep it current with each release. Use a standard format such as SPDX or CycloneDX so tools can read it. Include component names, versions, licenses, and the source of each artifact. Add build provenance so you can trace how code moved from repository to image.
Connect SBOMs to continuous vulnerability intelligence. Sync with trusted CVE feeds and enrich with exploitability data and safety impact. Rank issues by how they affect braking, steering, powertrain, charging, or data privacy. Focus remediation on items that are both reachable and dangerous in the current architecture. Where an SBOM is missing, run binary composition analysis to identify third-party code.
Build clear workflows for triage and fixes. Open a tracked ticket for each high-risk finding. Assign an owner. Define the control that will reduce the risk and the test that will prove it. Use VEX or an equivalent approach to mark non-exploitable cases and avoid noisy patching. Record exceptions with an expiry date and a review plan.
Push the same discipline into your supply chain. Flow ISO/SAE 21434 requirements into contracts and purchase orders. Ask suppliers for SBOMs, coordinated disclosure policies, and patch SLAs. Verify maturity with recognized programs such as VDA, ISA, or TISAX, and perform spot audits for critical components. Require secure delivery of artifacts and signed attestations that match what you integrate.
Operate the process like a program, not a fire drill. Set a regular cadence for SBOM updates and vulnerability reviews. Share findings with your Product Security Incident Response Team and with the teams that run OTA campaigns. Track a small set of metrics that show real progress. Measure SBOM coverage across ECUs and services. Measure the time to triage and fix high-severity CVEs. Watch the percentage of suppliers that meet security SLAs and hold them accountable when they do not.
Pillar 7. Continuous detection: IVN IDS + vSOC
Build continuous visibility into how the fleet operates so you can identify abuse before it escalates into an incident. Deploy an in-vehicle intrusion detection system that observes CAN, automotive Ethernet, and gateway traffic, then learn what normal looks like for each model, ECU variant, and firmware level. Extend monitoring to telematics, mobile apps, and public APIs, since attackers often pivot through cloud surfaces rather than starting on the bus.
Correlate signals across the edge and the cloud. Let the vehicle raise compact events for spoofing attempts, abnormal diagnostic requests, message floods, and failed update checks. Enrich those events in the backend with fleet context, software versions, and recent OTA activity, then group them into useful stories that an analyst can act on. Tune detections with realistic negative testing so you reduce false positives without blinding yourself to subtle attacks.
Establish a Vehicle Security Operations Center that oversees triage, escalation, and coordination. Define runbooks for containment, rollback, and forced update, and tie them to your Product Security Incident Response Team and OTA program so fixes move quickly from decision to deployment. Share threat intelligence with suppliers and collect learnings after every event so detections improve with each release.
Measure outcomes to demonstrate the system's effectiveness. Track detection dwell time, the share of alerts triaged within SLA, the actual positive rate, coverage of monitored interfaces per model, and sensor health across the fleet. Keep data only as long as necessary and apply privacy safeguards to ensure that monitoring strengthens security without creating new risks.
Pillar 8. Verification like attackers
Adopt an adversarial mindset across vehicles, apps, and cloud services. Prioritize pen-testing for ECUs, gateways, telematics, mobile apps, and backend APIs. Let threat models drive scope, success criteria, and data handling rules. Use independent testers when possible and coordinate with safety teams to manage test risk.
Go beyond functional tests with fuzzing and fault injection. Blast protocol stacks with malformed frames and odd state sequences. Vary timing, voltage, and bus load to expose race conditions and brownout behavior. Run long soak tests to catch issues that only appear under sustained stress.
Bake conformance and negative testing into every release gate. Validate UDS and DoIP behavior, certificate and TLS handling, and access control for diagnostic sessions. Exercise V2X message validation and replay defenses. Confirm that debug paths and factory modes are locked in production builds.
Treat regression as non-negotiable after any firmware or backend change. Re-run pen tests and fuzzing on the affected surfaces and adjacent systems. Cover hardware variants with hardware-in-the-loop and software-in-the-loop rigs. Preserve artifacts, traffic captures, and reports so that audits and root-cause analysis can move faster.
Track a small set of outcome metrics. Monitor the density of findings by subsystem and the verification rate of fixes. Measure time to close critical issues and the re-open rate. Record conformance pass rates and total fuzz hours per interface. Watch for test escapes that reach the field and drive them down over time.
Pillar 9. Incident response and PSIRT for fleets
Prepare before trouble starts and make roles unambiguous. Define who leads, who approves, who communicates, and who handles evidence across engineering, legal, customer support, and supplier management. Write playbooks for containment, rollback, credential revocation, and accelerated OTA, and align them with safety procedures so actions never increase physical risk. Run realistic table-top exercises and post-mortems on a fixed cadence, then update the playbooks with what you learned.
Establish a Product Security Incident Response Team that owns coordination from the initial signal to full recovery. Connect vSOC alerts, PSIRT triage, and OTA operations so detection turns into action without delay. Utilize clear severity classes, on-call rotations, and decision logs to maintain pace during high-activity events. Share relevant indicators with Auto-ISAC and critical suppliers, and fold lessons back into TARA, SDL gates, and CSMS audits.
Measure the program with a few numbers that matter. Track mean time to detect, contain, and recover. Track the percentage of high-severity incidents that follow the playbook. Track the rate of repeat incidents stemming from the same root cause and reduce it.
Pillar 10. People and culture
Treat security as a team sport rather than a specialist task. Give engineers, QA, operations, and dealership staff role-based training that maps to the systems they touch. Secure diagnostic and service tooling with strong authentication, least privilege, and audit trails. Pair developers with security coaches during design and code reviews so knowledge spreads through everyday work.
Establish a practice routine that is relevant to your needs. Run phishing drills that mirror current attack trends. Refresh secure-coding skills with examples taken from your own defect history. Celebrate teams that identify and address risky patterns early, and make it safe for employees to report issues without fear of blame. Tie personal goals to concrete outcomes such as passing security gates on the first attempt and reducing recurring defect classes.
Track a small set of culture metrics to see progress. Monitor training completion and retention. Monitor simulated phishing failure rates and time to patch training-related weaknesses. Monitor the share of releases that pass security checks without last-minute escalations.
Conclusion
Modern vehicles change rapidly, and the threat surface evolves accordingly. The only durable defense is a lifecycle program that blends strong engineering, fast operations, and a learning culture. The ten practices in this guide work best as a system. TARA keeps priorities fresh. SDL blocks risky code before it ships. Trusted boot and sound key management anchor identity. Segmentation and hardened interfaces cut blast radius. OTA with rollback delivers fixes safely at fleet scale. SBOM workflows and supplier assurance keep components known and patchable. Continuous detection turns signals into action. Adversarial testing finds what routine checks miss. PSIRT closes loops during real incidents. People and training make the whole program stick.
Pick two or three moves to start this quarter and measure them honestly. Prove coverage. Prove time to patch. Prove incident response speed. Then expand.
If you want a partner to operationalize these routines, contact Svitla Systems. We can help you build the muscle so security improves with every release.
Abbreviation Glossary
- ADAS — Advanced Driver Assistance Systems
- API — Application Programming Interface
- Auto-ISAC — Automotive Information Sharing and Analysis Center
- CAN — Controller Area Network
- CD — Continuous Delivery (or Deployment)
- CERT C — CERT Secure Coding Standard for C
- CI — Continuous Integration
- CSMS — Cybersecurity Management System
- CVE — Common Vulnerabilities and Exposures
- DoIP — Diagnostics over Internet Protocol
- ECU — Electronic Control Unit
- EU — European Union
- GPS — Global Positioning System
- HSM — Hardware Security Module
- IDS — Intrusion Detection System
- ISO/SAE 21434 — International Organization for Standardization / Society of Automotive Engineers standard for road-vehicle cybersecurity engineering
- IVN — In-Vehicle Network
- MISRA C — Motor Industry Software Reliability Association C coding guidelines
- OTA — Over-the-Air (software updates)
- PSIRT — Product Security Incident Response Team
- SBOM — Software Bill of Materials
- SLA — Service Level Agreement
- SPDX — Software Package Data Exchange
- SSDL / SSDLC — Secure Software Development Lifecycle (appears as “SSDL” in the intro)
- TARA — Threat Analysis and Risk Assessment
- TLS — Transport Layer Security
- TPM — Trusted Platform Module
- TISAX — Trusted Information Security Assessment Exchange
- UNECE — United Nations Economic Commission for Europe
- UDS — Unified Diagnostic Services
- vSOC — Vehicle Security Operations Center
- V2X — Vehicle-to-Everything
- VDA ISA — Verband der Automobilindustrie Information Security Assessment
- VEX — Vulnerability Exploitability eXchange
- WP.29 — World Forum for Harmonization of Vehicle Regulations (UN vehicle regulations body)





![[Blog cover] How to build a secure DevOps cycle](https://svitla.com/wp-content/uploads/2025/07/Blog-cover-How-to-build-a-secure-DevOps-cycle-560x310.jpg)