The flip side of digital transformation in healthcare care is heightened cybersecurity risks. Globally, 92% of healthcare organizations experienced a cyberattack in 2024. Across the EU, 309 institutions reported a significant cybersecurity incident.
Healthcare cybersecurity risks are on the rise because of the high value of patient and doctor data. Stolen personal identifiers can be sold for identity theft, insurance, or prescription fraud – all of which are rampant. The sector’s critical need to maintain uninterrupted patient care increases the likelihood of paying ransoms in ransomware attacks, incentivizing hackers.
In this guide, we’ll look at the most acute cybersecurity threats in healthcare and the most effective mitigation strategies.
Top 5 Cybersecurity Threats in Healthcare
Cybersecurity for hospitals and healthcare facilities starts with understanding the risk landscape. The top threats in this sector include ransomware, phishing, social engineering, DDoS attacks, cloud, and medical IoT vulnerability exploits.
Ransomware
Ransomware – malicious software encrypts data and demands payment for its release – is the most rampant type of cybercrime, especially in healthcare. Through 2024, there were 149 ransomware attacks on global healthcare institutions.
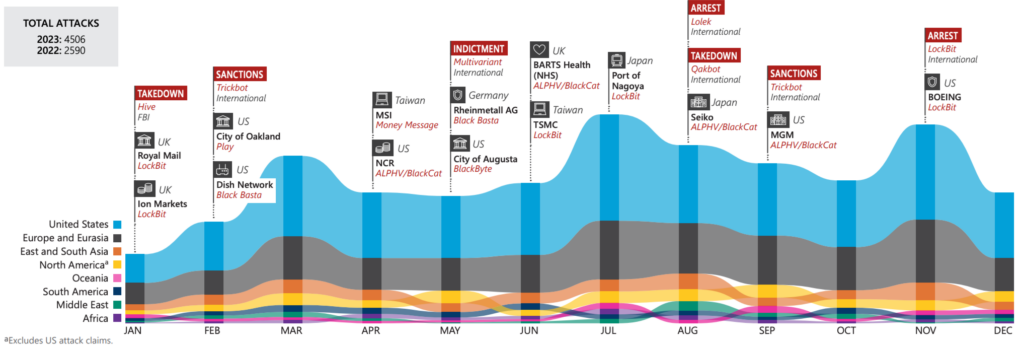
In February 2024, The BlackCat/ALPHV ransomware group targeted Change Healthcare in the US, stealing 6TB of data including medical records, insurance details, and personal information of over 100 million patients (approximately one-third of the U.S. population). Apart from data loss, the attack also caused a nationwide disruption of electronic payments, medical claims, and e-prescription services, forcing many healthcare providers to suspend operations temporarily. Change Healthcare was forced to pay a $22 million ransom. The total losses reached $3.09 billion by year-end, accounting for system restoration and response effort direct costs.
Unfortunately, ransomware attacks often succeed because healthcare institutions rely on legacy IT infrastructure with known security vulnerabilities, which creates easy entry points for attackers. For example, many exploit unsecured Citrix portals and outdated EHR system versions to distribute malicious software.
Phishing and Social Engineering
Phishing attacks trick users into revealing sensitive information, such as clicking a fraudulent link in a text or email message and then inputting their login/pass info at a sham website.
Social engineering, in turn, is a more elaborate strategy for divulging confidential information from people with access to confidential information or privileged account access. For example, a hacker may be impersonating the company’s CISO and asking other executives to share their system access credentials.
Because both are relatively easy to orchestrate, they severely undermine medical cybersecurity. Cybercriminals managed to access the data of over 366,000 patients at Rocky Mountain Gastroenterology Associates by compromising one email account. SAG-AFTRA Health Plan and East Paris Internal Medicine Associates also suffered major healthcare data breaches last year because of phishing attacks.
Moreover, hackers can also target patient portals to gain access to other connected systems, which further increases the defense perimeter for healthcare institutions.
DDoS Attacks
Distributed denial of service (DDoS) attacks overwhelm target IT infrastructure with massive bogus traffic from different sources, causing service disruption and downtime. They’re relatively easy and cheap to orchestrate, so hackers often use them as a ‘smoke screen’ to thwart healthcare IT security resources’ attention from their brute force penetration attacks.
On average, healthcare providers experience over 415 million DDoS attacks per year, causing major operational disruptions. In November 2024, the healthcare system of Singapore suffered a total outage of all healthcare services requiring Internet connectivity due to a massive DDoS attack, delaying patient care.
Unlike ransomware, DDoS attacks more often have a state-backed or activism component. For instance, NoName057(16), a pro-Russia hacktivist group, has been pestering public and private institutions with application-layer DDoS attacks more aggressively through 2024, leading to a 43% incident rise.
Medical IoT Vulnerabilities
The increased volume of cyber attacks in healthcare is also partially caused by greater reliance on medical IoT devices – remote patient monitoring systems, telemedicine platforms, medical wearables, and IoT-enabled medical equipment.
While most devices go through rigorous security testing as part of the certification processes, poor IoT network configuration, outdated patches, weak authentication mechanisms, and lack of transmitted data encryption turn these into security risks. A staggering 85% of connected surgical devices run with outdated operating systems – one of the easiest vulnerabilities for hackers to exploit.
Moreover, university researchers have successfully tampered with some of the latest model oximeters and smartwatch devices, used in clinical settings. They succeeded in intercepting transmitted healthcare data and exposing sensitive patient details.
Cloud Vulnerabilities
Cloud technologies in healthcare enabled telemedicine, virtual patient care, real-time data sharing, faster diagnostics, and accelerated drug development, among other advancements. However, just like medical IoT devices, the lack of proper cloud security controls has also resulted in greater cyber exposure.
Dutch Medical Lab held unsecured records on a public cloud server. Over 1.3 million records were exposed when a hacker discovered that major oversight. In general, suboptimal (or missing) identity and access management (IAM) controls are one the prime causes of cloud data leaks. Non-secured application programming interfaces (APIs) and misconfigured cloud settings for accessing storage are two other problems. These are baseline cybersecurity responsibilities of all cloud users, which many, unfortunately, treat as an afterthought.
Bonus: Third-Party Vendor Risks
Rounding up our list of the biggest cybersecurity threats in healthcare are third-party dependencies. Healthcare organizations rely on a growing number of ecosystem partners, ranging from insurers and medical device suppliers to accounting and workplace management software providers
This makes it easier for attackers to cause a daisy-chain disruption by targeting the weakest link in an ecosystem. For example, several unprotected healthcare APIs exchange data between an EHR and an e-pharmacy platform.
Thirty-four US healthcare organizations were affected by a ransomware attack on OneTouchPoint – a popular healthcare mailing and printing vendor. OTP didn’t notice a breach in their system for several months. By that time, attackers have successfully made their way to OTP’s clients including Blue Shield of California, Kaiser Permanente, Anthem, and Blue Cross.
Best Practices for Mitigating Top Cybersecurity Threats in Healthcare
Cybersecurity risks in healthcare are rising, but countermeasures have also advanced. However, many healthcare organizations still practice a ‘reactive’ approach to cybersecurity – invest in systems for incident mitigation rather than prevention.
Switching to a more effective, proactive cybersecurity approach to eliminate exploit opportunities is a far better option.
1. Implement Healthcare Staff Training in Cybersecurity
In many cases, human errors lie at the bottom of the security chain, so regular security awareness training is essential. It’s vital to train staff to recognize phishing emails, suspicious links, and social engineering tricks.
Leaders still skim on regular employee training. Only 59% of healthcare organizations offer regular cyber-training and awareness programs to all staff. Most only focus on HIPAA compliance refreshers or baseline training during onboarding.
That’s not enough as the threat landscape rapidly evolves. Users feel more vulnerable. According to an EY survey, 78% are concerned about AI usage in cyberattacks, and another 39% doubt they can use AI responsibly.
A good cybersecurity training program for healthcare workers should be:
- Regular. Cyber awareness training should be administered every quarter for most roles. This can be a combination of formal workshops, e-learning classes, and periodic simulations (e.g., a phishing attempt, done by your cybersec department) to ensure proper knowledge retention.
- Role-based. Customize program content to different user groups (e.g., clinicians, administrative staff, IT personnel) to train them to better recognize and respond to security risks they’re facing.
- Practical. Coach your people on the exact steps they should take if they suspect an attack or a breach. Provide step-by-step instructions for reporting suspicious activity to your cybersecurity departments and doing baseline damage mitigation.
2. Implement Strong Authentication and Access Controls
Your cyber-protection is as strong as its weakest link – usually your user authentication methods. The lack of multifactor authentication (MFA) and simple, repeatable passwords compromise network security.
Implement role-based access control (RBAC) policy – an adaptive approach of automatically assigning predefined permissions to user groups for accessing different types of applications or data storage systems. With modern identity solutions like Microsoft Entra ID or Okta, you can eliminate the time and errors associated with manual access management, which often leads to privilege creep or orphaned accounts, apply more granular policies, and regularly review access permissions.
A good RBAC policy aligns access rights to asset types with your IT policies. For example, only senior IT staff can permanently delete data backups or access select API configurations. Roles are typically defined by user attributes like office, department, position, and seniority. You can auto-enforce separate policies for third parties like software vendors or insurers.
Strong authentication methods, such as MFA and password-less authentication, also make unauthorized access significantly more difficult. MFA combines two or more credentials for user authentication, for example, a password and a text message or a FIDO security key with email notification, thus, adding an extra security layer (like a mobile code or token) beyond just a password. This is critical for defending against phishing and credential theft, as MFA can thwart an attacker even if they obtain a user’s login details.
A risk-based authentication approach is optimal for preventing most cybersecurity issues in healthcare without over-taxing users. Instead of enforcing a blanket policy of always using MFA even for accessing local, isolated applications, implement adaptive policies based on factors like user behavior, device trust, and location. Say, if a doctor signs on to the EMR from a known local device with a validated IP from an office site without any issues, you can avoid asking them to use a Passkey to access approved records.
Risk-based authentication requires advanced user behavior monitoring systems to detect anomalies in real-time with a low false positive rate. You may need to invest in extra cybersecurity solutions.
3. Regulary Update Software Systems
Regular software patching and updates are critical. Many healthcare cyber hacks happen due to vulnerabilities in outdated software. Create a routine vulnerability scanning schedule using tools like Nessus, Microsoft Defender for Cloud, or AWS Inspector to conduct assessments and plan updates.
4. Implement Network Segmentation
Network segmentation is an extra measure for sensitive cloud workloads. NSA and CISA recommend using the “macro segmentation principle” by default – separate IT resources for different teams into different tenant administrator groups. Disable SSH on all non-essential cloud instances. Configure public IP addresses only for production instances that need them.
For more critical systems, consider additional “micro-segmentation” measures: Only allow necessary data flows for normal operations. There should be no communication path if two cloud applications don’t need to exchange data. If they only need to communicate telemetry data, only one-way exchanges should be allowed.
Virtual Private Networks (VPNs) offer an extra safeguard. The VPN encrypts data sent between remote devices and the healthcare network to ensure that sensitive information remains confidential and is protected during transit.
5. Defend Against DDoS Attacks
DDoS mitigation strategies prevent disruptions to critical systems. This type of attack can overload hospital networks, making electronic health records (EHRs), telemedicine platforms, and online patient portals inaccessible. To protect against DDoS attacks:
- Deploy a DDoS protection service from providers like Cloudflare, Akamai, AWS Shield, or Microsoft Azure to filter out malicious traffic before it reaches hospital networks.
- Implement rate limiting and traffic filtering on firewalls and network devices to block excessive requests from suspicious sources.
- Use load balancing and network redundancy to distribute traffic across multiple servers and prevent single points of failure.
- Monitor network traffic for anomalies using SIEM tools or AI-driven detection systems that can flag unusual activity early.
- Develop a DDoS response plan with predefined actions, including emergency failover solutions for critical services.
6. Implement Disaster Recovery Plans (DRP) and Incident Response Planning
DRP
Regularly back up all critical data, including patient records, and store backups offline or in a secure, segmented environment. An effective backup is often the key to a quick recovery after a ransomware attack. Test backup restoration periodically to ensure the data can be recovered since many organizations only discover their backups were failing after an attack.
Apart from cybersecurity, healthcare operations can also get paralyzed by natural disasters, power cuts, and human error. Staff oversight and errors caused data loss and exfiltration at 31% of healthcare organizations last year – meaning too few have effective DRP in place.
A DRP is a set of standard operating procedures for recovering normal IT system performance, following an unforeseen event – be it a DDoS attack or a sudden server failure. Healthcare organizations should implement full services failover to backup cloud sites for essential business systems (e.g., an EHR, EMR, and patient management systems) and local data storage facilities, hosting critical data.
Failover is a backup process that auto-transfers a service operation from a failed system to a standby alternative, ensuring continued accessibility for users despite disruptions. Automatic failovers should be implemented for all business-critical healthcare applications, databases, servers, and networks. Larger healthcare organizations should consider multiple data redundancy sites to compensate for regional disruptions in cloud services availability or use hybrid architecture, combining cloud and on-premises failover sites.
To ensure your DRPs function as they should, run periodic drills to sharpen your procedures and address oversites.
Incident response planning
Alongside backups, have a detailed incident response plan that covers cyber incidents. This plan should define roles (who contacts whom, who leads the technical response, how to communicate during downtime). Ideally, exercise the incident response plan with drills. Healthcare entities should also include contingencies for maintaining patient care during IT outages – for instance, printed forms for charting, emergency contact lists, and so on. Being prepared to respond swiftly can dramatically reduce the impact of an attack. Integrate lessons learned from past incidents and continuously update it.
7. Encrypt Data and Strengthen Privacy
HIPAA-compliant software with sensitive personal data must ensure full protection of data at rest and in movement, requiring proper data encryption.
You can choose either the Commercial National Security Algorithm (CNSA) Suite or the National Institute of Standards and Technology (NIST) recommended algorithms, which include block cipher techniques, hash functions, and randomness beacons.
To secure the keys use secure generation, storage, and rotation practices:
- Set key expiration dates to minimize risks from compromised keys.
- Add a multi-person approval process for key access to avoid a single point of failure.
- Keep a log audit of key usage, access attempts, and rotations for threat monitoring and compliance tracking.
- Use Public Key Infrastructure (PKI) or key exchange protocols like Diffie-Hellman to distribute keys safely among teams.
- Apply data masking, tokenization, and encryption to safeguard the most sensitive records.
- Lastly, assign appropriate decryption accesses based on your RBAC policy to further defuse the risks.
8. Manage Third-Party Risk
Given the reliance on cloud services and contractors, it’s vital to assess and monitor the security of partners. Common measures include: risk assessments, asking about their security practices, and signing Business Associate Agreements (BAAs) that commit them to protecting the data.
Essentially, treat vendor security as an extension of your own – share threat intelligence with key partners and collaborate on drills if possible. Supply chain cyberattacks can be devastating, so proactive communication and contractual safeguards with vendors are key to reducing that risk.
9. Conduct Periodic Security Audits
Cybersecurity isn’t a one-time task. It’s an ongoing technology and cultural initiative to create robust system safeguards and minimize risk exposures to known and emerging threats.
A good practice is to host periodic security audits – a hands-on investigation into your current protection state. Alongside annual audits, schedule interim ones after adopting new healthcare technology or modernizing legacy systems. The goals of such audits are:
- Identifying security threats and vulnerabilities
- Evaluation of the likelihood and impact of data breaches
- Assessment of current security measures’ effectiveness
- Recommendations for extra safeguards based on risk levels.
Security audits help stay in sync with regulatory changes. Following its report, the Office for Civil Rights (OCR) suggests making all existing Security HIPAA Rule measures “required”, rather than “addressable”. The Healthcare Cybersecurity Improvement Act, pending Congressional review, will require hospitals to establish basic cybersecurity standards as a Medicare Condition of Participation. A security audit can help you proactively prepare for these changes.
Conclusion
Cybersecurity for healthcare providers is non-negotiable. The direct and indirect costs of a data breach or a ransomware attack are substantially higher than the implementation of the above best practices.
Whether you’re looking to implement new software or secure existing cloud infrastructure, the Svitla Systems healthcare software development team would be glad to assist. We have successfully helped global healthcare providers establish strong user security, harden networks and data storage, and achieve HIPAA compliance. Contact us for more information.

![[Blog cover] Top cybersecurity issues in healthcare](https://svitla.com/wp-content/uploads/2025/03/Blog-cover-Top-cybersecurity-issues-in-healthcare-936x527.jpg)
![[Blog cover] Digital transformation technologies in healthcare](https://svitla.com/wp-content/uploads/2025/02/Blog-cover-Digital-transformation-technologies-in-healthcare-560x310.jpg)

![[Blog cover] Benefits of iot in healthcare](https://svitla.com/wp-content/uploads/2025/02/Blog-cover-Benefits-of-iot-in-healthcare-560x310.jpg)