To trust or not to trust — that is the question, especially in cybersecurity. You’ve definitely heard sayings like never trust, always verify; check twice, trust once; or trust but confirm. Today, these are more than just life wisdom, but the core Zero Trust Architecture principles. As the digital ecosystem becomes more complex and cybersecurity threats continue to evolve, traditional perimeter-based security models are no longer as effective as they once were. Astoundingly, 95% of security breaches are caused by human error despite existing perimeter controls. This is where Zero Trust Architecture (ZTA) comes to the rescue. Its use of conditional access, continuous authentication, dynamic trust evaluation, and the principle of least privilege strengthens security across various domains.
Is ZTA a good fit for your organization?
Are there any challenges to consider before implementing the Zero Trust approach?
How to implement Zero Trust Architecture into your business process to maximize benefits?
Find answers to these and other related questions in our dedicated article.
Understanding Zero Trust Architecture
Gartner classifies Zero Trust as a security model that clearly identifies users and devices, giving them only the necessary access needed for the business to run smoothly while minimizing risks.
ZTA introduces a new access control model centered on ongoing authentication and conditional permissions to reduce cyber risks. It applies the principle of least privilege, granting users, devices, and processes access to resources on a per-request basis, depending on confirmed credentials. Unlike conventional approaches, ZTA continuously authenticates identities throughout communication, boosting security in adaptable environments and modifying access rights as necessary.
According to the National Cyber Security Center, the fundamental Zero Trust Architecture principles are as follows:
- Understand your architecture by identifying users, devices, services, and data.
- Assess the health and behavior of users, devices, and services.
- Implement policies to authorize requests and ensure authentication and authorization are in place everywhere.
- Concentrate your monitoring efforts on users, devices, and services.
- Do not trust any network, including your own, and choose services built for Zero Trust.
The core idea of ZTA is straightforward but groundbreaking:
Believe that no device, user, or service is automatically trustworthy.
This signifies a major shift from traditional security methods, which saw networks as either "inside" (trusted) or "outside" (untrusted).
| Traditional Perimeter Security | Zero Trust Security | |
| Perimeter Security | Depends on a network perimeter as a trust boundary | Removes the idea of a trusted internal network |
| Trust Assumption | Presumes the credibility of users and devices on the network | Never trusts by default, regardless of location |
| Access Management | Often determined by network location | Determined by identity, device status, and multiple contextual aspects |
| Network Design | Castle-and-barrier system emphasizing perimeter protection | Distributed and micro-segmented with precise access management |
| Incident Response | Once the perimeter is overcome, intruders face no restrictions | If a breach is detected, attackers' actions are thoroughly tracked |
In a nutshell, here are the key Zero Trust Architecture benefits as compared to traditional security models:
- Streamlined security management
- Reduced operational complexity
- Adaptable for large-scale user groups
- Enhanced transparency and control
- Upgraded compliance measures
- Decreased expenses through reduced reliance on costly hardware and software.
Preparing for Zero Trust Architecture Implementation
Before diving into the preparation process, it is important to assess how much your business actually needs Zero Trust Architecture implementation, or if it even does.
Does your organization need ZTA?
The simplest method to recognize this is by answering the following questions:
- Have you encountered difficulties with traditional cybersecurity approaches?
- Are you aware of micro-segmentation and its role in limiting breaches?
- Is your approach to managing insider threats effective in a dynamic IT environment?
- Do you need ongoing compliance with regulatory standards?
| Interesting fact Gartner analysts forecast that by 2026, over 50% of cyberattacks will target areas outside the scope of Zero Trust controls, which they cannot prevent or mitigate. |
Zero Trust Architecture Tenets
If you’ve determined that ZTA is the right fit for your business, which is likely, you now need to prepare for its implementation. Organizations considering Zero Trust Architecture implementation should choose the approach best suited to their environment. They must balance risk profiles with access methods and define the Zero Trust scope clearly. The National Institute of Standards and Technology recommends building a mature ZTA around seven key tenets.
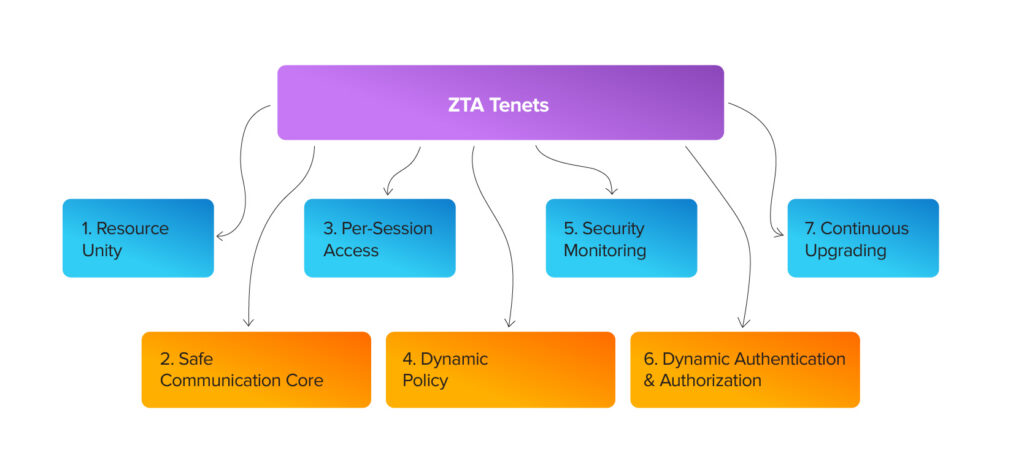
- All data sources, services, and devices, including personal ones accessing company resources, are treated as resources within a network composed of multiple device classes.
- All communication is secured, ensuring confidentiality and authentication, regardless of network location or device ownership.
- Enterprise resource access is granted per session with trust verified and minimal privileges, without automatic access to other resources.
- Access to resources is managed by flexible rules that consider factors like who is requesting, what device they are using, and where or when the request is made. Organizations secure their data by identifying their assets, determining who should access them, and setting boundaries based on security requirements and risks.
- The enterprise continuously monitors the security and integrity of all devices and never automatically trusts any asset. Devices with vulnerabilities or lacking proper management may be restricted or denied access, making strong monitoring and patching systems essential.
- The system verifies and enforces authentication and authorization before granting access. Organizations rely on identity tools, multifactor authentication, and continuous monitoring to manage and secure access continuously.
- The enterprise collects and examines data on assets, network traffic, and access requests to enhance security and develop smarter access policies.
Aligning Business Goals with Security
To synchronize your business objectives with ZTA, start by understanding your organization's mission and key priorities:
- Work with executives to identify key assets and translate security needs into business language, focusing on safeguarding revenue and customer trust.
- Develop a strategic plan that connects Zero Trust initiatives to outcomes such as business continuity and compliance, securing executive support and collaboration across teams.
- Set SMART (Specific, Measurable, Attainable, Relevant, Time-bound) security goals linked to business KPIs and start Zero Trust Architecture implementation with high-value assets for quick wins that can grow over time.
- Use frameworks like NIST CSF or ISO 27001 to structure your approach and regularly update your strategy to stay aligned with evolving business needs and threats.
Assessing the Current Security Posture
Evaluating your organization’s current security posture within ZTA requires a thorough understanding and inventory of assets, transaction flows, risks, and policy gaps related to encryption and identity verification.
These key steps will help you conduct a comprehensive assessment:
- Asset inventory: Carefully compile a list of all users, devices (including IoT), applications, data, and network components to determine what needs protection. Ongoing logging and categorization are crucial.
- Modelling transaction flows: Chart how data moves through systems and networks to distinguish normal activity from anomalies and identify access points that need regulation.
- Risk identification: Analyze vulnerabilities and potential attack routes by examining asset security, device compliance, and behavioral indicators.
- Policy and controls review: Evaluate current access policies, authentication methods, encryption practices, and monitoring systems to identify shortcomings. Ensure access decisions are dynamic, context-aware, and adhere to least privilege principles.
Additionally, micro-segmentation provides visibility that informs posture assessment.
Micro-segmentation aids by dividing the network into smaller, secure zones with specific security rules. This detailed segmentation enhances visibility into network traffic and asset protection, making it easier to identify and isolate risks within each segment. By enforcing strict “least privilege” access controls at this level, micro-segmentation decreases the chances of attackers moving laterally if one area is compromised.
Note: Micro-segmentation is not the same as ZTNA. ZTNA manages application access session-by-session based on identity, device, and risk factors, while micro-segmentation restricts east–west communication within the environment at L4/L7 layers. This section evaluates the readiness and visibility required for both layers.
Building Efficient Cross-Team Collaboration
Joint teamwork makes ZTA operate more efficiently by helping IT, security, and operations teams talk more openly, share common goals, and work together smoothly. When everyone is on the same page, security rules match the business needs and systems more closely, which means risks get spotted and handled faster with fewer mistakes. Here are the items to consider:
- Having clear and open ways to talk and share ideas is crucial for smooth teamwork across different groups in the process of Zero Trust Architecture implementation. Things like discussion boards and real-time editing tools help everyone work together better and share information easily.
- Staying in regular touch helps spot and deal with potential risks early so that you can respond faster to security issues. Automated alerts also help stay ahead of problems and keep everyone on the same page about the project.
- Enhancing communication between departments and fostering collaboration becomes more manageable with project management tools and shared dashboards. Additionally, regular training on effective communication practices further boosts team competence and cooperation.
Step-by-Step Guidelines on How to Implement Zero Trust Architecture
Implementing Zero Trust security requires careful planning and gradual steps. Here's a clear guide to help your organization set it up.
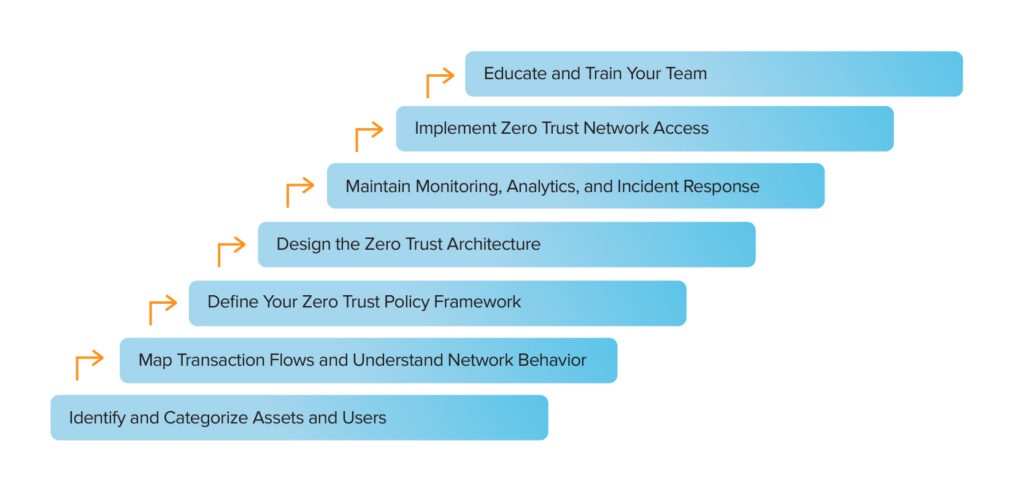
Step 1: Identify and Categorize Assets and Users
Start by identifying and organizing everyone and everything connected to your network. This forms a clear “protect surface” to direct your security efforts.
- Users: list employees, contractors, and third parties, noting their roles, access needs, and data requirements
- Devices: track all connected devices, such as personal phones, IoT gadgets, and company laptops, and verify their security status
- Resources: record physical items like servers, infrastructure, and virtual assets like cloud tools, databases
- Key risks: highlight sensitive data, critical apps, physical equipment, and services that support daily operations.
Also, consider using advanced tools for analysis, keep your lists updated, and integrate with security systems via APIs.
Step 2: Map Transaction Flows and Understand Network Behavior
To strengthen security with Zero Trust, map how data flows between users, devices, apps, and services. This helps identify normal patterns, risks, and weaknesses to improve access controls.
- List DAAS (Devices, Assets, Applications, and Services) elements: Catalog all devices, assets, apps, and services with input from stakeholders.
- Track users and access: Record all human and non-human users accessing systems.
- Spot dependencies: Identify internal and external factors impacting your security scope.
- Analyze data movement: Use monitoring tools to trace data paths across systems.
- Manage encryption: Monitor encrypted traffic using metadata or controlled decryption.
- Sharpen security: Continuously refine boundaries based on flow insights.
Step 3: Define Your Zero Trust Policy Framework
A ZTA policy sets the foundation for a secure network because it defines how users and devices are authenticated and authorized. Since it is developed before the architecture, the policy ensures alignment with security principles. Using the Kipling Method, craft robust policies by examining:
- Who: Verify user identities via trusted sources like active directories
- What: Limit access to role-essential resources using RBAC (role-based access control)
- When: Restrict access to specific times to prevent unauthorized use
- Where: Allow access only from approved locations or IPs
- Why: Require justified access requests tied to roles
- How: Enforce secure protocols like VPNs or HTTPS.
Step 4: Design the Zero Trust Architecture
Create a detailed blueprint that uses ZTA ideas to protect your organization's assets and data. This plan should include specific rules, policies, and technology tools that work together to keep everything secure in a flexible and ongoing way.
- Core components: Use Policy Enforcement Points, Policy Decision Points, and continuous monitoring to manage access securely
- Context-aware access: Verify requests based on identity, device health, location, and behavior
- Integration: Ensure compatibility with on-premises, cloud, and legacy systems.
- Protect surface: Focus security on critical assets and data
- Policies: Align fine-grained rules with business goals
- Monitoring: Enable real-time analytics and anomaly detection
- Phased rollout: Implement gradually for scalability.
Step 5: Implement Zero Trust Network Access (ZTNA)
Set up ZTNA to protect your organization’s resources. It uses strong, flexible controls so that no user or device is automatically trusted, helping keep everything secure.
Key aspects of ZTNA implementation include:
- Dynamic access: Replace VPNs with identity- and context-based access, verifying user identity, device health, and location continuously.
- Secure channels: Use tunnels or gateways to authenticate and authorize all requests, denying non-compliant access.
- Policy integration: Centralize decisions with a Policy Engine and Enforcement Points for consistent access control.
- Hybrid support: Secure on-premises, cloud, and edge resources seamlessly.
- Monitoring: Use real-time analytics to detect and respond to threats swiftly.
Step 6: Maintain Monitoring, Analytics, and Incident Response
Keep an eye on network activity, analyze network behavior, and respond quickly to any security issues. This way, your organization will stay flexible and protected.
The main elements of this step are:
- Ongoing monitoring: Track users, devices, and traffic in real time to spot anomalies and threats.
- Smart analytics: Use AI and SIEM (Security Information and Event Management) systems for early detection of suspicious patterns.
- Adaptive controls: Adjust access dynamically based on real-time risk insights.
- Incident response: Set up workflows for quick detection, investigation, and resolution of security events.
- Compliance checks: Use monitoring data to ensure policies align with regulations and audit needs.
Step 7: Educate and Train Your Team
Make sure everyone involved understands the basics of the new cybersecurity approach, including the Zero Trust Architecture principles, policies, and how it works day to day. This helps ensure everyone is on the same page and can work together effectively to maintain strong security.
Here are the key points to consider:
- Clear understanding: Train executives, IT, security teams, and users on concepts like least privilege and continuous verification.
- Role-specific training: Tailor education for architects on policy design, IT on controls, and leaders on business alignment.
- Ongoing learning: Keep teams updated on evolving threats and best practices to maintain a security-focused culture.
- Change management: Use structured programs to boost collaboration and integrate ZTA into daily operations.
- Certifications: Leverage programs like CCZT (Certificate of Competence in Zero Trust) or ISC2’s Zero Trust Strategy Certificate for professional expertise.
Use Cases of Zero Trust
In 2021, the U.S. government required all federal agencies to adopt Zero Trust security measures by the end of fiscal year 2024. The Department of Defense is also leading the way with a Zero Trust plan, aiming to fully implement it by 2027. This involves steps like requiring multi-factor authentication, encrypting all internal communications, and logging every access request. But why is this happening? Here are some common practical examples of ZTA that are prompting even the biggest and most influential organizations to make the switch to Zero Trust.
Reducing the Risk of Data Breaches
NIST Special Publication 800-207 explains that Zero Trust security helps reduce data breaches by not automatically trusting any user, device, or network. Instead, it requires ongoing checks to verify identities and permissions. The system uses small segments within the network to prevent intruders from moving freely if they get in, keeping potential threats contained. CISA’s Zero Trust Maturity Model emphasizes that detailed access controls and real-time monitoring lower the chances of an attack because they ensure only authorized people can reach specific data or systems. Besides, NIST points out that flexible authentication and authorization rules can stop unauthorized access to sensitive information, even if someone’s login info is stolen.
Saving on Cybersecurity
According to CISA, adopting a ZTA makes security operations more efficient through centralized policies and automation. By bringing together identity, device, and application security into one clear system, organizations can reduce the complexity and cost of managing many different security tools. NIST SP 800-207, in its turn, supports this idea by promoting security rules that use existing infrastructure, which helps avoid the need for expensive new hardware. CISA also points out that moving from the basic to the advanced level of Zero Trust maturity helps make better use of resources. Automated monitoring and management reduce the need for manual work, which can lower ongoing operational costs.
Supporting Regulatory Compliance
NIST SP 800-207 offers a clear approach for ongoing security checks, giving users least-privilege access and keeping detailed logs. These steps help organizations meet important standards like GDPR, HIPAA, and FISMA. CISA’s Zero Trust Maturity Model was created to support Executive Order 14028, which requires federal agencies to use Zero Trust security practices to follow federal cybersecurity rules. CISA makes sure agencies stay compliant by providing visibility into systems, encrypting data, and controlling access. NIST points out that ZTA’s way of classifying and protecting data helps organizations follow privacy laws by keeping sensitive information safe and preserving audit trails.
Managing Third-Party Risks
NIST SP 800-207 recommends continuously verifying the identity and permissions of all users and devices, including external vendors and partners, before granting access to resources. The Zero Trust approach makes sure that third-party connections are limited to only what they need to do, which helps reduce the risk of supply chain attacks. CISA’s Zero Trust Maturity Model focuses on checking device compliance and using risk-based policies to control access, especially for unmanaged devices. For federal agencies, CISA advises applying Zero Trust Architecture principles to external collaborators as well, making sure their access is monitored and kept limited to prevent any unauthorized data exposure.
Securing Remote Work
According to CISA, it's essential to have device authentication, verify user identities, and control secure access for people working outside traditional network boundaries. ZTA helps eliminate the need for VPNs by offering direct and secure access to applications and data. The NIST SP 800-207 explains that Zero Trust keeps remote access safe through dynamic, context-aware policies that check user behavior, device health, and network conditions. Both NIST and CISA emphasize that with continuous monitoring, ZTA makes sure remote workers stay secure, even on unsecured networks, by enforcing the principle of least privilege and preventing lateral movement.
Enhancing Cloud Security
The NIST Special Publication 800-207A, which accompanies SP 800-207, focuses on applying Zero Trust Architecture principles in cloud environments. It highlights how Zero Trust protects cloud workloads by using identity-based access, encryption, and continuous monitoring, especially across multi-cloud and hybrid setups. CISA’s Zero Trust Maturity Model adds to this by including the Application Workload and Data pillars, which help secure cloud applications and data through techniques like micro-segmentation and increased visibility. NIST stresses that policy enforcement points (PEPs) are key to maintaining consistent security across distributed cloud environments, helping to prevent unauthorized access. Overall, CISA’s model guides organizations in adopting Zero Trust Architecture principles such as least-privilege access and real-time threat detection, both of which are vital for safeguarding cloud-native applications.
Common Challenges in Zero Trust Architecture Implementation and Solutions to Them
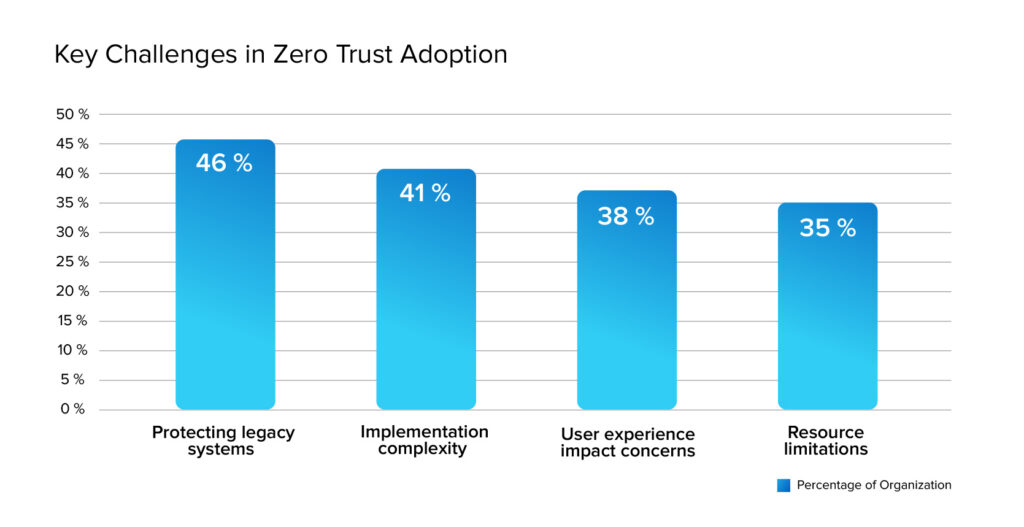
Source: World Journal of Advanced Research and Review
Protecting Legacy Systems
Protecting older systems within a ZTA is challenging because they often rely on implicit trust, use outdated APIs, and have limited monitoring, which can lead to security gaps, interoperability issues, and technical debt. Examples include old databases and devices that make it harder to use features like multi-factor authentication (MFA), organize data, and monitor system activity. According to NIST SP 800-207 and CISA’s ZTMM v2, this increases the risk of mistakes and vendor lock-in.
To address these issues, organizations should take inventory of all assets, set up segmentation gateways, and use CISA’s automation tools to modernize systems gradually. It's also important to budget for necessary updates, adopt MFA methods resistant to phishing, and run pilot projects for migration. Working with vendors and CISA’s Continuous Diagnostics and Mitigation (CDM) program can help ensure systems work well together, balance security with day-to-day operations, and follow the Zero Trust Architecture principles.
Legacy Integration & Exceptions
Parts of any environment will inevitably run on older protocols or without modern SSO/TLS (OT/ICS, thick clients, printers, legacy apps). To make Zero Trust effective today, we follow Contain → Broker → Wrap → (Refactor/Retire): isolate such assets in deny-by-default segments and broker all access via a proxy/PEP with MFA and session recording; where feasible, “wrap” traffic with TLS/reverse proxy; in parallel, plan refactoring or retirement. Any deviations are handled as time-boxed exceptions with a risk owner and compensating controls. This reduces blast radius, restores visibility in blind spots, and aligns with NIST SP 800-207 (transitioning to ZTA via PE/PA/PEP), NIST SP 800-82 (segregation/bastions for ICS), and CISA ZTMM v2 (eliminating implicit trust in legacy environments).
Complex Access Policy and Implementation
Zero Trust Architecture implementation requires ongoing verification and integration across different systems, leading to challenges like compatibility, scalability, limited visibility, and cultural changes, according to NIST SP 800-207 and CISA’s Zero Trust Maturity Model. To simplify the process, organizations should adopt phased implementation, enhance asset visibility through inventories and monitoring, use automation tools for risk-based policies, secure policy components, train staff, and connect with cloud environments via micro-segmentation and continuous updates to maintain a good balance between security and usability.
Besides access policies, ZTA implementation can be demanding in terms of computing resources, staff training, and handling legacy systems. Organizations also face challenges with silos, governance gaps, and adapting to hybrid or federated systems. Phased overhauls can increase technical debt and costs. To assist, agencies like DHS and NASA recommend centralized governance, maintaining asset inventories, having dedicated experts, and testing new approaches gradually. Following NIST and CISA's models supports a scalable, effective adoption.
UX Impact Concerns
ZTA can make things tricky for users. Constant logins, new workflows, and strict access rules can annoy people, slow them down, or make them resistant to change. Plus, extra security checks might cause delays. To fix this:
- Use smart login systems that adjust based on risk, like single sign-on to cut down on password prompts
- Automate access rules for smoother work
- Train users to understand Zero Trust Architecture benefits
- Test changes in small groups first
- Use cloud-based tools to keep things fast and create policies that fit user roles, balancing security and ease.
Resource Limitations
Many businesses face limited budgets, a lack of skilled staff, and infrastructure issues. According to WJARR, 41% of organizations mention that complexity is a major barrier. These issues can slow down progress, especially for organizations with legacy systems or little experience with cloud technologies. To overcome this, it's recommended to:
- Start with security focused on identity management, which helps make better use of resources
- Consider phased deployment, where the most valuable assets are protected first, to control costs and reduce complexity.
- Additionally, using existing tools like service meshes and API gateways can avoid extra costs. Incorporating ZTA into DevSecOps practices early on reduces the need for extra resources and helps improve security step by step across the organization.
Measuring Success and Continuous Improvement
Defining KPIs and Metrics
Here’s a concise chart summarizing the KPIs and metrics to measure the success of a Zero Trust Architecture efficiently.
| KPI / Metric | What It Measures | How to Track or Use It |
| Attack‑Surface Contraction Rate (ASCR) | Tracks how effectively the organization is minimizing its externally exposed assets and systems. | Use tools like Shodan or asset scanners to find public-facing resources; prioritize high-risk areas by sensitivity. |
| Mean Time to Detect & Validate (MTTD‑V) | Measures how quickly potential threats are noticed and verified by analysts. | Log the time between initial activity and detection, and between detection and human confirmation. |
| Policy Enforcement Accuracy (PEA) | Evaluates how often security controls either incorrectly block legitimate actions or fail to block malicious ones. | Periodically audit access logs; aim to reduce both false positives and false negatives to minimal levels. |
| Credential Hygiene Index (CHI) | Indicates the overall health of identity and access controls, including password practices, MFA, and privilege use. | Build a composite score using data from identity providers, PAM tools, and secret managers; set targets and track improvements. |
| Micro‑Segmentation Coverage Ratio (MSCR) | Reflects the extent to which systems and workloads are protected using identity-aware segmentation. | Measure the portion of systems that have policies applied out of the total; work toward near-total coverage. |
| Risk‑Adjusted Cost per Connection (RACpC) | Assesses the average cost of enabling secure connections, adjusted for the level of risk. | Divide total ZTA costs by total session volume weighted by risk level; monitor this trend over time. |
| Security‑Debt Velocity (SDV) | Shows the rate at which unresolved security issues (e.g., legacy systems or misconfigurations) are being addressed. | Track how many known issues are resolved each cycle; faster velocity indicates progress in reducing technical risk. |
Continuous Policy Refinement
Continuously improving security policies in a Zero Trust framework is an ongoing process. It involves regularly updating policies based on current data and new threats. To measure progress, organizations look at clear goals, such as:
- Fewer security breaches
- Faster threat detection
- Better compliance.
They also track specific metrics such as failed login attempts and access to sensitive information to find gaps and improve controls. This ongoing effort helps keep policies aligned with business goals, making the security system more agile and strong. Regular reviews and data-based changes, as recommended by ISACA and Microsoft, help create more effective and sustainable cybersecurity practices.
Ensuring Compliance
Ensuring your business follows the rules in a ZTA framework is crucial for tracking success and continuously improving over time. This means sticking to laws like GDPR, HIPAA (depending on the industry), or standards such as NIST 800-53 by using strict access controls, constant monitoring, and keeping detailed records.
- Key measurements like how often policies are broken or how quickly audits are completed help show how well you're doing.
- Regular checks, as suggested by organizations like NIST and CIS, help find areas where you might not meet the standards, so you can update your policies accordingly.
- Automated tools help observe user actions and system access to keep everything in line with rules.
Constantly improving these processes helps lessen risks and strengthen security, building trust and responsibility in a constantly changing threat landscape.
Summing Up
Ultimately, authenticating every user, device, and application before access greatly reduces the risk of security breaches and unauthorized network activity. This way, a Zero Trust approach drastically lowers the chances of data leaks and system vulnerabilities, potentially saving your organization substantial costs due to security incidents. And don’t be discouraged by the cost of initial investments in tools and training. The long-term savings from preventing breaches, operational downtime, and compliance penalties make it a smart decision for both the security and financial stability of any organization.
And if you want to delegate cybersecurity tasks to an external team of experts, there’s another option. Entrust your organization’s cybersecurity to Svitla to keep even the most sensitive data protected like a bank vault with retina scans.



![[Blog cover] Common AI security risks](https://svitla.com/wp-content/uploads/2025/05/Blog-cover-Common-AI-security-risks-560x310.jpg)

