What is penetration testing?
A penetration test (or pen test) is the method of a computer system simulation to detect cybersecurity vulnerabilities. Penetration testing of a network, application, device, and/or physical security is performed to detect any vulnerabilities which would allow possible penetration from inside or outside of the organization and thus prevent damage and information leaks. As a result of a pentest, a special document is created listing the details of the test vulnerabilities that were found. The recognized problem areas are reconfigured or replaced by more effective security systems and instruments.
Why is pen testing important?
First of all, penetration testing allows for detecting problems before security breaches happen. This minimizes the risk of data loss, information leaks, service damage, and other problems.
Penetration testing is a scheduled procedure and is a part of security audits. Frequency of pen testing is defined by requirements for each organization type, for instance, “Payment Card Industry Data Security Standard”.
James P. Anderson defined the following steps for information security procedures:
- Find an exploitable vulnerability
- Design an attack around it
- Test the attack
- Seize a line in use
- Enter the attack
- Exploit the entry for information recovery
As usual, it is better to predict risks and fix problems before they happen. It allows for avoiding all potential problems caused by unauthorized access to information systems and services by:
- Determining the possibility of a certain set of attacks
- Identification of high-risk vulnerabilities
- Identifying vulnerabilities that can be difficult or impossible to find by using automated tools for vulnerability scanning
- Assessing the size and value of the potential impact of successful attacks on business
- Testing the ability of network protectors to successfully detect and respond to attacks
Types of penetration testing
Selecting the proper type of testing will allow the detection of existing problems in the security of the information system or organization.
There are many types of penetration testing:
- White box pen test
- Black box pen test
- Covert pen test
- External pen test
- Internal pen test
When choosing a Black Box level, the penetration tester knows only the range of external IP addresses. This approach is as close as possible to the actions of the hacker; data about the tested object will be collected using open source, social engineering, etc.
In White Box mode, the penetration tester has much broader information. In this case, experts can be provided with documentation, source code, network structure, and full access to the object being tested.
In Black Hat mode, only managers of the managing service are aware of the test. In this case, it is possible to check the level of operational readiness for attacks by network administrators and IT administrators.
In the White Hat mode, the test executors are in constant contact with the client's IT service, and the customer’s IT-specialists do not interfere with the performance of the required tests. The main task is to identify possible vulnerabilities and assess the risk of penetration into the system.
How to do penetration testing
How to do penetration testing? First of all, it includes the following steps:
- Analysis of available sources
- Scanning by tools
- Analysis/evaluation of identified vulnerabilities and recommendations
- Preparing a report
Then it is necessary to define the area of penetration testing:
- Application
- Network
- Web
- Physical
- IoT/Sensors
A Penetration test can be performed manually or in an automated mode.
Manual pen testing can be either the focused or comprehensive type. Both types are valuable and should be scheduled according to the security plan. A Manual penetration test requires an expert engineer to perform it while automated penetration testing can be executed as a standard activity by a system administrator. Manual pen testing gives more details about specific problems of the system; on the other hand, automated testing results in a list of more items to be checked.
For automated testing, many tools can be used, and using a combination of them produces better results. The following are tools for automated testing: OpenVAs
- Burp Suite
- Metasploit Project
- Nessus
- Nmap
- OWASP ZAP
- w3af
The following operation system (OS) distribution can be used as well:
- BlackArch
- BackBox
- BackTrack Linux
- Parrot Security OS
- Pentoo based
- WHAX
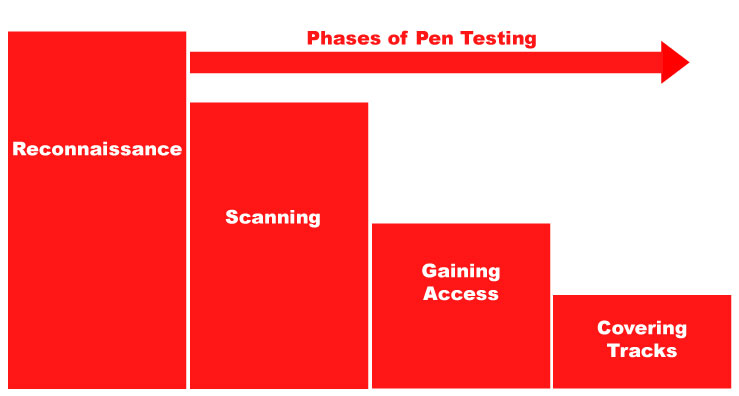
Pen testing has five phases, the size of each phase depends on the target and plan of the specific system configuration.
The report provided to a customer on the penetration test results, contains a detailed description of performed work, all detected vulnerabilities and how they are implemented. The report also may contain specific recommendations for eliminating vulnerabilities.
Methodologies and Standards of Pen Testing
OSSTMM (Open Source Security Testing Methodology Manual) is a peer-reviewed methodology for conducting security tests. OSSTMM test cases are divided into five channels that are tested together: information and data management, personnel security awareness levels, fraud and social engineering levels, computer and telecommunication networks, wireless devices, mobile devices, physical access control, and physical locations.
The list of methods allows selecting the most suitable approach for a specific situation:
- OWASP testing guide
- PCI testing guide
- Testing Execution Standard (PTSE)
- NIST 800-115
- Testing Framework
- Information Systems Security Assessment Framework (ISSAF)
- Open Source Security Testing Methodology Manual (“OSSTMM”)
- FedRAMP Testing Guidance
- CREST Testing Guide
NIST (National Institute of Standards and Technology) discusses penetration testing in SP800-115. The NIST methodology is less exhaustive than the OSSTMM, regulators may accept it more willingly.
And finally Penetration Testing Execution Standard (PTES) defines it as the following steps:
- Pre-engagement Interactions
- Intelligence Gathering
- Threat Modeling
- Vulnerability Analysis
- Exploitation
- Post Exploitation
- Reporting
This allows constructing and execution of penetration testing on the level of black box testing or white box testing after the manual or automated procedure. Each of these steps is critical to the overall result and cannot be skipped.
Frequency of Penetration Testing performance
Penetration testing is meant to save an organization from costly cyber attacks.
Usually, it should take place at least once per year. For many organizations, this frequency is enough if there is no critical data or vitally important information.
However, some organizations should plan pen testing quarterly. For instance, organizations with large data sets of user information, companies and enterprises’ web sites, etc. should carry outa different kind of pen testing every 3 months.
Organizations which deal with critical data should plan testing monthly. All financial organizations, demanding infrastructures, medical services, etc. must plan white box/black box testing every 30 days.
Finally, for some organizations, pen testing is a part of a weekly or daily routine. These are transport information systems, power plants, government organizations, etc., who must plan for almost constant health-checks (including employees). For such organizations, it is required by standards of corporate or government rules.
Also, it is recommended to do pen testing (at least in automated mode) after changes in system configuration, network upgrade, firewall reconfigurations or employees management.
Takeaways
Penetration testing can save organizations from costly information leaks, disasters or service malfunction. It reduces risks on information systems’ security on many levels: hardware, software, and human factors.
Detailed testing reports should be taken very seriously by the administration and top management, and all potential problems must be fixed and documented.
It is always better to detect problems before they happen.





